Building HIPAA-Compliant Software: Requirements, Development Plan & Estimated Costs


In today’s healthcare landscape, data security and privacy have become critical concerns due to the increasing amount of sensitive health information being exchanged across various platforms. The Health Insurance Portability and Accountability Act (HIPAA), enacted in 1996, serves as the cornerstone for healthcare data protection in the United States. It ensures the privacy and security of patient data while promoting the exchange of information between healthcare providers, insurers, and other stakeholders in a secure and compliant manner.
HIPAA compliance is not just a regulatory necessity for healthcare providers and organizations; it is a business imperative. Failure to comply with HIPAA regulations can result in hefty fines, legal repercussions, and most importantly, a loss of trust from patients and clients. This is where HIPAA software comes into play. HIPAA software refers to custom-built or third-party solutions specifically designed to meet the rigorous security, privacy, and operational standards set forth by HIPAA.
Building HIPAA-compliant software involves more than just ensuring basic functionality. It requires embedding robust security features like data encryption, access control, auditing, and backup systems that align with the regulations to protect patient information (Protected Health Information or PHI). Additionally, HIPAA-compliant software must be scalable, integrate with existing healthcare systems, and offer easy navigation and usability for healthcare professionals.
This blog aims to provide an in-depth understanding of what HIPAA software is, the key features that make software HIPAA-compliant, the steps involved in building such software, the associated costs, and the challenges that organizations might face during the development process. Understanding these factors is essential for healthcare providers, developers, and businesses looking to develop software solutions that are not only functional but also fully compliant with HIPAA regulations.
When developing software for healthcare purposes, ensuring that it meets HIPAA compliance requirements is not optional—it’s a necessity. HIPAA-compliant software must adhere to specific standards and regulations to safeguard sensitive healthcare data, such as Protected Health Information (PHI). These features are critical in securing data, maintaining patient privacy, and facilitating the smooth and secure exchange of information. Let’s explore some of the most essential features that HIPAA-compliant software must include:
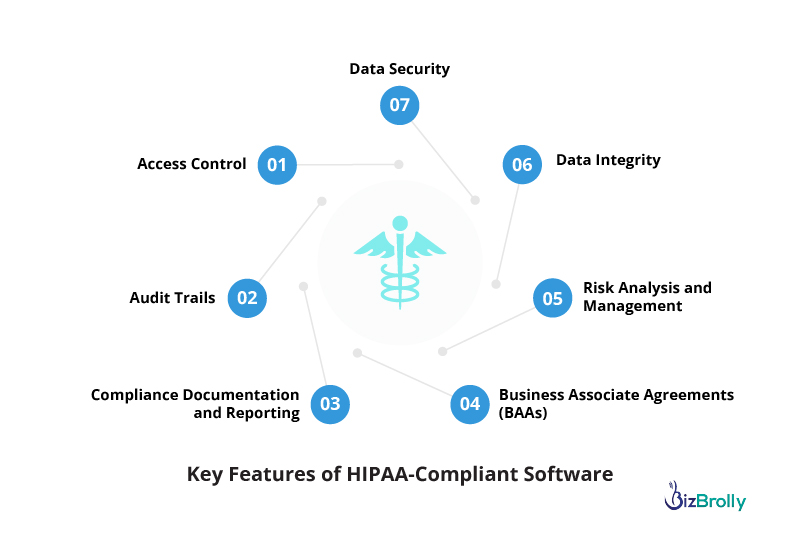
Data security is the cornerstone of HIPAA compliance. Healthcare providers, insurers, and other organizations that handle PHI are legally obligated to ensure that this data is protected from unauthorized access, tampering, or theft. HIPAA-compliant software employs robust security measures, including:
These security measures prevent unauthorized access and guarantee that sensitive healthcare data remains safe, a fundamental requirement under HIPAA regulations.
Access control mechanisms are vital for ensuring that only authorized personnel can access PHI. HIPAA-compliant software must incorporate robust role-based access control (RBAC) systems that enforce the principle of least privilege. This means that users are only granted access to the data necessary for their job functions. Key elements include:
With strong access control mechanisms, organizations can ensure that their employees only access the data required to perform their duties, reducing the risk of accidental or intentional data breaches.
Audit trails are an essential component of HIPAA-compliant software as they provide a detailed, time-stamped record of all user actions. This feature is crucial for tracking and investigating any suspicious activity or data access. HIPAA mandates that organizations maintain audit trails to demonstrate accountability and transparency regarding PHI access. Some key points about audit trails include:
Audit trails are an important security feature as they not only help in detecting potential breaches but also provide evidence that can protect organizations from legal or financial liabilities in case of a breach.
Data integrity ensures that PHI remains accurate and unaltered. Maintaining the accuracy of healthcare data is essential for patient safety, clinical decision-making, and regulatory compliance. HIPAA-compliant software must support data integrity through mechanisms such as:
By ensuring data integrity, HIPAA-compliant software helps to ensure that patient records are reliable, preventing errors that could compromise care or violate regulatory standards.
HIPAA requires healthcare organizations to enter into Business Associate Agreements (BAAs) with any third-party vendors that will have access to PHI. These agreements outline the responsibilities of the vendor regarding data protection, breach notification, and compliance. HIPAA-compliant software should include features that help manage and track BAAs, including:
By incorporating BAA management features, HIPAA-compliant software ensures that healthcare organizations meet their regulatory obligations when working with third-party vendors.
HIPAA requires healthcare organizations to conduct regular risk assessments to identify potential vulnerabilities in their systems that could expose PHI to unauthorized access. HIPAA-compliant software should include features that facilitate continuous risk management:
Risk analysis tools within HIPAA-compliant software help organizations stay proactive in identifying and mitigating threats to patient data.
Keeping track of HIPAA compliance requires significant documentation and reporting. HIPAA-compliant software should provide built-in tools for tracking compliance activities and generating reports for audits. Key features include:
These tools simplify compliance management, ensuring that healthcare organizations can demonstrate ongoing adherence to HIPAA regulations.
Building HIPAA-compliant software requires a thorough and systematic approach, ensuring that every aspect of the software development process aligns with the strict security and privacy standards outlined in HIPAA. These steps are not only essential for compliance but also for creating a software solution that will function effectively in a healthcare environment while safeguarding Protected Health Information (PHI). Below are the key stages involved in the development of HIPAA-compliant software:
The first step in building any software, including HIPAA-compliant solutions, is to clearly understand the requirements of the stakeholders, such as healthcare providers, insurers, patients, and regulatory bodies. This stage involves:
During this phase, it’s critical to define the scope of the software’s functionality, understand the specific privacy and security requirements, and outline the technical and compliance considerations that must be adhered to.
Once the requirements have been clearly defined, the next step is the design phase, where the system architecture and user interfaces are designed. This phase should emphasize both functionality and compliance. Key elements include:
During the design phase, it’s important to ensure that the user experience doesn’t compromise security, and that the architecture of the software ensures that PHI is stored and transmitted securely.
With a solid design in place, the next step is the development phase. This is where the actual coding and implementation of features happen. It is crucial during this phase to focus on both the functionality of the software and maintaining compliance with HIPAA. The key activities involved in the development phase are:
Throughout development, the primary focus should be on securing the code, protecting data, and ensuring that all the necessary security features are embedded into the software. Regular code audits and penetration testing should be part of this phase to ensure compliance with HIPAA’s security requirements.
After development, a rigorous testing phase is necessary to ensure that the software meets all functional, security, and compliance requirements. This phase is essential for identifying vulnerabilities or areas where the software may fail to meet HIPAA standards.
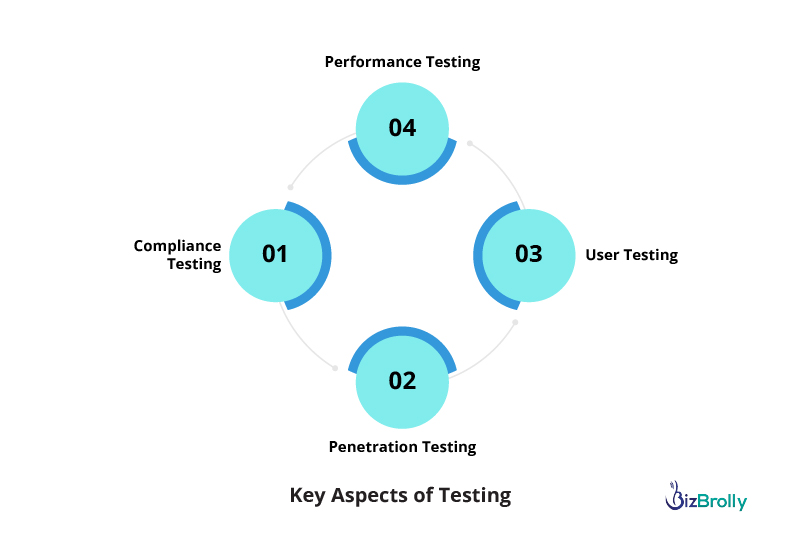
At this stage, it’s important to test the software for vulnerabilities and confirm that it meets all the necessary standards for HIPAA compliance. This testing phase should also include third-party audits, if applicable.
Once the software has passed all testing and is deemed compliant with HIPAA regulations, it is ready for deployment. This phase involves preparing the system for use in a live environment and ensuring that all stakeholders are trained on how to use it effectively and securely. The steps involved include:
Deployment should be carefully planned to ensure a smooth transition and to prevent operational disruptions. Regular updates and ongoing user support are critical for maintaining long-term compliance with HIPAA regulations.
HIPAA compliance is not a one-time effort; it is an ongoing responsibility. The healthcare environment and data security landscape are constantly evolving, so software solutions need to be updated regularly to stay compliant with the latest regulations and security standards. This includes:
When developing HIPAA-compliant software, organizations must ensure that the application meets stringent security and privacy standards for handling Protected Health Information (PHI). This involves various costs associated with development, security, compliance, and ongoing maintenance.
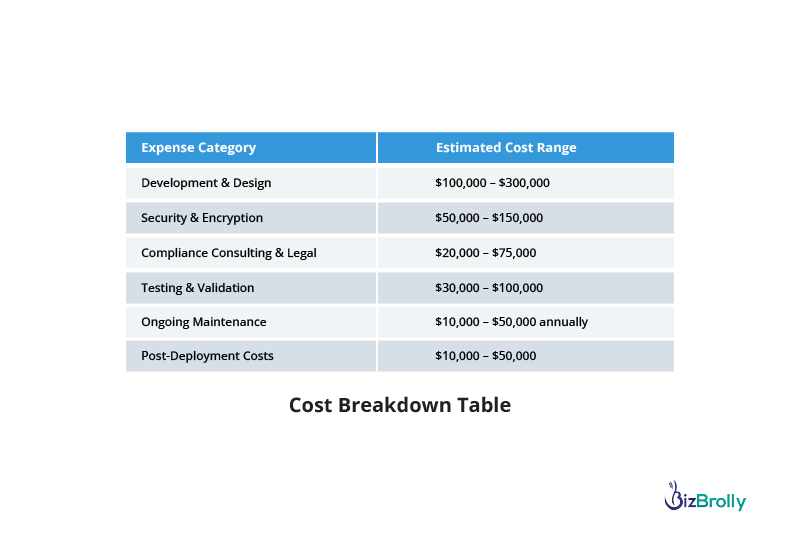
Building HIPAA-compliant software is a complex and costly endeavor, but it’s crucial to ensure the protection of sensitive health data and avoid costly penalties. BizBrolly Solutions understands the intricacies of HIPAA compliance and offers expert guidance throughout the entire software development lifecycle. From design to deployment, our team ensures that every aspect of your application adheres to HIPAA’s stringent privacy and security requirements.
We provide comprehensive services to help you navigate the development of secure applications, including integrating robust security features like encryption, secure authentication, and detailed audit trails. Our experienced team works with you to implement the necessary safeguards to protect sensitive patient information while ensuring seamless functionality for your business.
At BizBrolly, we understand that each business is unique, which is why we offer tailored solutions to meet your specific needs and compliance goals. We assist with everything from choosing HIPAA-compliant hosting providers to ongoing security maintenance and updates.
With BizBrolly Solutions, you can confidently build HIPAA-compliant software that not only meets regulatory standards but also offers peace of mind to your customers. Contact us today to learn how we can support you in developing secure, compliant healthcare applications.

In the healthcare sector, safeguarding patient data is not just a regulatory req...
Explore more
In the evolving landscape of healthcare, the focus has steadily shifted towards ...
Explore more


D-23, Sector 63, Noida,
UP - 201307
141 Westgate Dr, Edison,
NJ - 08820

4 Black lion court, Mill road, Kent, UK – ME71HL

2207, 2220 Lakeshore Blvd W, Toronto ON- M8V0C1

94A Central Road, Jacanlee, Johannesburg 2194