
Blockchain is the technology used by developers of cryptocurrencies, like Bitcoin, to enable the exchange of financial “coins” between participants in the absence of a trusted third party to ensure the transaction, such as is typically done by governments. Blockchain has evolved to become a generic approach to store and process data in a highly decentralized and secure way.
All blockchains work to make decentralized nodes achieve an agreement on the total order of transactions through cryptography and an underlying consensus mechanism. Technically, blockchains generally fall into one of two categories: permissionless or permission. Permissionless blockchains allow anyone to participate, are considered “open,” and have trust provided by algorithms. In contrast, permission blockchains are usually “private” or “consortium” and all participant identities are known but no participant needs to be trusted. In reality, variants exist where there is no clear line between different types of blockchains. For instance, Ethereum, a typically permissionless blockchain, can be set up as a private blockchain called the Ethereum private network. Efforts have also been made to achieve anonymity for permission blockchains.
Basics of the blockchain technology market
A Layered View of Blockchain
Blockchains can be abstracted into three different layers. At the core of blockchain is layer 1: BFT consensus—also known as state machine replication—which is a generic approach to tolerate failures. BFT consensus has different forms, ranging from conventional BFT protocols to PoW-based consensus. Despite fundamental differences in how consensus is achieved, any form must solve the same problem: how to enable nodes to reach consensus on the total order (i.e., consistency) of transactions submitted by clients in the form of requests. After nodes reach a consensus about the order, the data/operations of the transactions are then processed according to the order of the transactions. As a result, distributed nodes functionally behave as if there were one centralized node. This ensures that there is only one sequence of client transactions, known as “the longest chain.” Layer 2 of blockchain is the smart contract, which is essentially software code. A smart contract provides an interface for blockchain developers to implement new functions. Smart contracts can then facilitate, verify, or enforce the execution of business transactions. A smart contract can be viewed as a program that connects the underlying consensus protocols with layer 3, applications, and uses cases.
Building the Hash Chain
The cryptographic concepts of “hashing” and “digital signatures” provide tamper-proofing and validation. One way hash functions generate a unique output of alphanumeric text given an input of a list of transactions. Change a single thing about the list of transactions and the resulting hash is significantly different. Digital signatures like Rivest–Shamir–Adleman or Elliptic Curve Digital Signature Algorithm are used to “sign” transactions. The hashes are then linked together in a chain of blocks, with any block except the first one, called the genesis block, pointing to prior hashes and signatures. Such a hash chain ensures that no one can manipulate the contents of any block or reverse the chain order.
Permissioned Blockchains
Permissioned blockchains provide consensus and security using provably secure distributed consensus protocols. The consensus protocols do not involve expensive procedures such as in PoW. Therefore, permission systems have low latency (the time between the client sending a transaction until the client receives a reply), they are also scalable (both in the number of clients and transactions as well as the number of servers), and they consume less energy than permissionless blockchains (described in detail later).
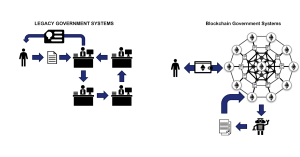
Most permission blockchains, especially those widely employed or piloted by the government, use provably secure BFT protocols. Among these BFT solutions, leader-based protocols are widely used, such as PBFT [30] and its variants [106, 108]. In these types of protocols, there is a specific leader, which proposes the order of transactions. The nodes then communicate with each other in several steps to reach an agreement on the order. In most leader-based protocols, each node sends messages to all other nodes in each step and collects matching messages from a fraction of nodes before moving to the next step. If the leader is potentially faulty or malicious, other nodes will run a leader change protocol until a new leader is elected.
2.4 Permissionless Blockchains
Most permissionless blockchains adopt a “Proof-of-Something” strategy. In the case of Bitcoin, this is PoW, a mathematical challenge offered to all nodes in the system to try to overcome (or work through) by an activity called mining. Once mined, a node can propose a block of transactions and get rewarded in Bitcoin if the proposal is accepted. The drawback to this approach is that throughput (the number of transactions processed per second) is limited, and the energy consumption is high. Furthermore, collusion occurs—nodes form cartel-like entities called mining pools—concentrating mining activity under the control of one group. With mining pools, the blockchain becomes less decentralized therefore less secure, and more susceptible to attack and manipulation.
Compared with BFT-based consensus, PoW-based consensus does not have a fixed leader and can be viewed as a system where the leader changes after each block of transactions. To propose a new transaction, a node needs to first solve PoW from the previous transaction. When a node proposes a transaction, it also generates a pseudorandom number that is called a cryptographic nonce. As illustrated in Figure 4, the nonce is broadcast to all other nodes. Nodes compete to become the next leader by selecting random pending transactions and generating a hash of the selected transactions. The node that first generates a hash smaller than the nonce value is the winner and becomes the next leader. Compared with BFT consensus, PoW-based consensus involves fewer messages for nodes to reach a consensus on the transactions. The blockchains based on it can easily scale to thousands of nodes. The challenge is that more than one node might solve the puzzle at the same time, creating a fork of the hash chain. Nodes in the PoW consensus will detect the fork, eventually agree on the longest hash chain, and use it. It takes time for each transaction to be finalized after it has been proposed, usually after six blocks, each taking about 10 minutes, in the case of Bitcoin—about an hour. This finalization time can be reduced using different approaches.
Interception of Blockchain technology through Asian government.
In 2019, the Filipino government endorsed the reception of Ethereum-based solutions for around 80 provincial banks to gain admittance to financial administrations. Propelling the work is the way that just 42% of Filipinos matured 15 or more established to have a financial balance because of a mix of elements
The idea of blockchain city has been utilized and made inhabit Malaysia’s Melaka Straits city, a traveler city financed by the Chinese government. The venture means to utilize the blockchain to follow traveler visas, travelers, gear, and booking administrations [102]. The city will likewise deal with its own token, the DMI coin, for vacationers to trade their cash into computerized monetary forms for installment in the city by means of their cell phones.
South Korea’s administration declared a 4B Korean won (about $3.5 million) grant to set up a blockchain-empowered virtual power plant in the city of Busan, the nation’s second-most crowded city. The power plant is to be cloud-based and ought to incorporate different energy assets to improve power age.